How to Organize Your Response to the 2024 National Public Data Breach

Hack! Breach! Data theft!
You see a news story about yet another company getting hacked, or you receive a letter from some service provider telling you that their servers were “breached.” Sometimes the letter offers advice, or perhaps a year of free credit monitoring.
Organizing your records, passwords, financial resources, and entire identity to protect against identity theft is exhausting. It would be understandable if you tend to tune out any news about such hacks and breaches.
Over the past week or so, however, you might have heard about a particularly nasty breach, leaving bad guys with access to millions of Social Security numbers. That probably made you sit up and take notice…and get queasy.
THE UNPRECEDENTED BREACH OF SOCIAL SECURITY NUMBERS AND MORE
At the outset, I should note that contrary to popular perception — the Social Security Administration was not hacked. The federal government wasn’t breached.

Who Got Hacked and When?
A Florida-based data brokerage company, National Public Data (NPD), got hacked. You may wonder how NPD got so much personal data in the first place. It, like many companies of its kind, scrapes data from wherever they can, including federal and state public records databases like voter registries, DMV records, professional license filings, birth/marriage/death records, criminal and civil course records, and non-public databases.
So, private information, by way of how the modern world works, gets stored somewhere over which we have no control, and then scraped, gobbled up by companies like NPD. They then turn around and sell our private data to anyone willing to pay — from employee background-check sites to private investigators (not cool, Sam Spade!) to data resellers.
According to NPD, the crime took place in December 2023; it just took a while to become known (and then a lot longer for NPD to own up to it). It’s not clear who actually stole the data.
What is clear is that the breach became known in on April 7, 2024, when a hacker group identified as USDoD posted on the dark web, offering an estimated 2.9 billion individual rows of data records for $3,5000,000. Jeez Louise!
At this point, various “bad actors” (by which I don’t mean David Hasselhoff or Pauly Shore) began posting on the dark web and leaking about the availability of the purloined data.
The breach was reported by the Daily Dark Web in a piece entitled NationalPublicData.com Hack Exposes a Nation’s Data:
The leaked data, which spans from the years 2019 to 2024, is of unprecedented magnitude, comprising 2.9 billion rows. The sheer volume of information involved is monumental, with the compressed data reaching 200GB to a staggering 4TB when uncompressed. The breached database includes comprehensive citizen information, firstname, lastname, middlename, name_suff, address,city, county name, phone 1,aka1 fullname, ssn and more. Such a massive breach raises serious concerns regarding data privacy, security, and the potential for widespread misuse or exploitation.
However, Daily Dark Web also noted that there was “a strong possibility that the assertion may be exaggerated and that the data could have been scraped from publicly available sources. Additional scrutiny and analysis are required to validate or refute these allegations.”
You’d expect that the mainstream media might attack this story like a dog with a bone, but few outlets took any notice. Instead, they focused on all the usual wars, natural disasters, sports, bird flu, Taylor Swift, and Congress trying to shut down TikTok.
Then, on July 21, 2024, someone leaked exactly what was stolen. Members of the cybercrime community Breachforums released in excess of 4 terabytes of data they claimed had been stolen (though not by them) from NPD.

Photo by Markus Spiske on Pexels.com
What Did the Hackers Get?
The breach contained massive database holdings at the nationalpublicdata.com domain, stealing Social Security records, phone numbers, physical address histories, and some email addresses of many millions of Americans. Information datasets from Canada and the United Kingdom were also included.
Per Troy Hunt, a regional director of Microsoft and founder of Have I Been Pwned (a site that helps people determine whether their email address has been included in data breaches), there were also 70 million rows from a database of U.S. criminal records.
Techcrunch referred to the data stolen as “partly legitimate — if imperfect.”
Brian Krebs of Krebs on Security further wrote that Atlas Data Privacy Corp. researchers found that there were 272 million unique Social Security Numbers in the entire records set, and that most of the records had a name, Social Security Number, and home address; approximately 26% of those records also included a phone number.
Apparently Atlas verified a subset of 5,000 addresses and phone numbers, and found that those records were, with “very few exceptions” for people born before January 1, 2002. So, maybe your college student is safe. But the rest of us? Oy.
Atlas also found that the average age of consumers in the records was 70 — with approximately two million records related to people who would be at least 120 years old at this point, so at least some of have already shuffled off this mortal coil, taking their credit lines with them.
This still leaves a lot of questions. Which data got out? Was it accurate or out of date? Which data was for deceased persons and which for real, live peeps? And what good data is paired with bad data?
If you’re feeling cyberwonky, read Troy Hunt’s Inside the “3 Billion People” National Public Data Breach. Hunt states that, “[t]here were no email addresses in the Social Security number files.” So, figuring out how bad it all is may take a while, because it’s hard to know what info is current and properly matched to your public identity.
Where Do Things Stand Now?
Mainstream media finally took notice on August 1, 2024, when California resident Christopher Hoffman filed a class action suit. Even then, NPD didn’t respond publicly until Friday, August 16, 2024, more than two weeks later, four months after the breach was originally reported, and more than eight months after the initial crime occurred!
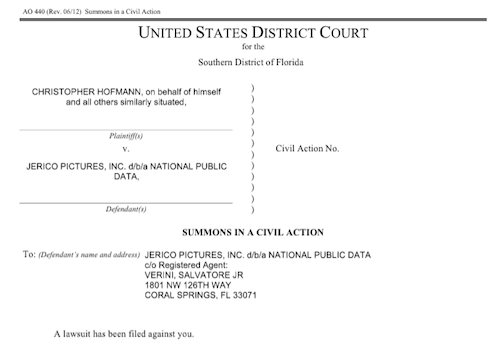
And when NPD finally did post a milquetoast-y comment, it merely said that the breach involved a “third-party bad actor that was trying to hack into data in late December 2023, with potential leaks of certain data in April 2024 and summer 2024.” Well, duh.
That’s not even all! According to two Bleeping Computer pieces, National Public Data Confirms Breach Exposing Social Security Numbers, and Hackers Leak 2.7 Billion Data Records with Social Security Numbers, on August 6, 2024, “another threat actor known as Fenice shared for free the most comprehensive variant of the database with 2.7 billion records, with multiple records referring to a single person” and further, the “threat actor known as “Fenice” leaked the most complete version of the stolen National Public Data data for free on the Breached hacking forum.”
Meanwhile, in finger-pointing worthy of the Spider-Man memes, this Fenice claimed that the data breach was actually conducted by a different threat actor named “SXUL” rather than USDoD. (What, nobody’s named Mike anymore?)
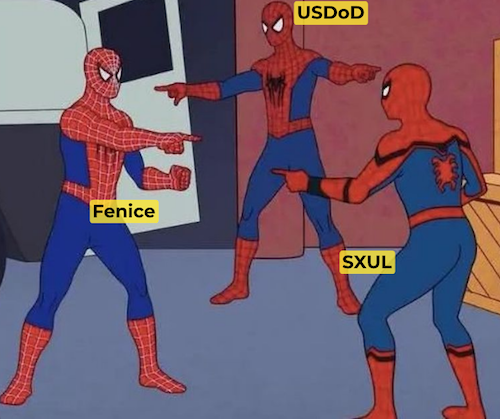
(I created this from a meme generator. Apologies for offended artistic tastes.)
So, our data was stolen, priced for sale for $3.5 million, and then offered up for free to hackers, but nobody told us regular folk until the lawyers wanted attention for a class action suit?
If you feel like you need an aspirin, you’re not alone. Nothing about this feels particularly organized. Or fair.
This class action suit is a big deal, because, as the plaintiff’s law firm explained in a press release, Hoffman was not a customer of NPD. None of us were.
Thus, unlike when we get those letters from our doctor’s office or credit card companies, we never voluntarily gave our personal information to NPD in the first place, so most Americans (and Canadians, and citizens of the UK) won’t even know if they’ve been affected by the breach until or unless something along a continuum from hinky to financially catastrophic happens.
As a result, it’s essential to take action and organize your resources against potential fallout.
HOW TO KNOW IF YOUR INFORMATION WAS HACKED
The cybersecurity firm Pentester accessed the files included in the breach and created a free database/breach check of the stolen information — but with Social Security numbers redacted, birthdates partially redacted, and phone numbers and street addresses in the clear.
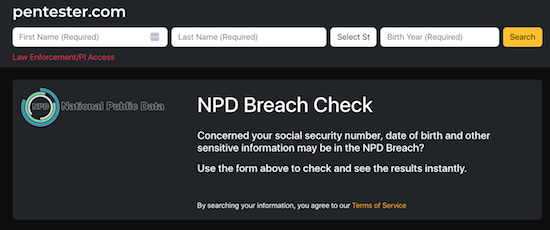
I know it doesn’t look very impressive, but experts and journalists, including at Time Magazine, have recommended using it.
Enter your first name, last name, state, and birth year. It will search billions of leaked records and note whether your information was included in the breach.
If your data isn’t found, you’ll get an error message instead of a list of records. Yay! Except that’s the starting point, not the finish line. Boo!
- Check every state you’ve lived in. Ever.
- Check your maiden name, or any other name by which you’ve been known, legally or otherwise.
- Check for your significant other, your parents, your kids, and pretty much everyone you care about. (I mean, you could also search for your horrible boss, the kid who stuffed you in a locker in seventh grade, and your ex-mother-in-law, just to enjoy a little schadenfreude. I won’t tell.)
However, will only tell you is whether your information is out there, somewhere, naked. Your next step is protect that data from molestation as best you can.
PROTECT YOURSELF AGAINST YOUR DATA BEING USED AGAINST YOU
Monitor your financial life
You should already be regularly checking your bank accounts and credit card statements for anomalies. Either log in to one at a time or use a financial dashboard like Empower, Rocket Money, or one of the other popular alternatives to the late, lamented Mint.
Next, monitor your credit reports.

Longtime Paper Doll readers know that I always advise using AnnualCreditReport.com, which, by law, guarantees a free credit report from each of the three credit reporting bureaus per year. Better yet, after the onset of the COVID pandemic and the related financial chaos that ensued, Equifax, Experian, and Trans-Union temporarily offered free weekly credit reports.
The bureaus extended those offers twice over the years, and as of last October, the Federal Trade Commission reported that AnnualCreditReport.com will now permanently make available weekly credit reports at no charge so that consumers can dispute errors, be watchful for any fraudulent account openings or changes, and report identity crimes at IdentityTheft.gov.
While you’re pulling your own credit report, pull them for your children, too. Even the existence of a credit report for a child who has never applied for credit is a big, honking sign that something fraudulent may have occurred.
Place a fraud alert on your credit file
This requires that any creditors contact you before making changes to any of the accounts you already have or before opening any new accounts in your name. You needn’t contact all three credit bureaus; rather, once you request a fraud alert with one bureau (say Equifax), the other two (Experian and Trans-Union) will be notified.
Per a law passed in 2018, fraud alerts stay in place for a full year (unless you rescind it earlier), and victims of identity theft and related crimes can secure an extended fraud alert for seven years. Previously, fraud alerts lasted only 90 days.
Also, the law requires that each of the credit reporting bureau must automatically send you a free credit report after you request a fraud alert. Scrutinize them carefully.
To request a fraud alert, contact one of the three credit bureaus’ fraud alert divisions:
- Equifax — or call 1-800-525-6285
- Experian — or call 1-888-397-3742
- TransUnion — or call 1-800-680-7289 (Note: an extended TransUnion fraud alert must be requested by mail.)
But before you choose this path, there’s a better option.
Freeze your credit file
A credit freeze is different from a fraud alert. While the fraud alert says that creditors have to contact you before changing or opening accounts, a freeze says, “Nope. Do not pass GO. Do not collect $200.” A freeze prevents any new loans or credit from being taken out in your name — even by you!
A credit freeze is different from a fraud alert. A fraud alert requires creditors contact you before changing/opening accounts; a freeze says, *Nope. Do not pass GO. Do not collect $200.* A freeze prevents any new loans/credit from… Share on XThe freeze stays in place until or unless you revoke it. So, if you need to buy a new car, seek a student loan or mortgage, or apply for a credit card, you can temporarily remove the freeze. After you secure funding, you can put the freeze back on.

Ice Photo by Enrique Zafra at Pexels.com
- Contact each of the three credit bureaus.
Unlike with the fraud alert, where you only have to contact one of the credit bureaus, you’ll need to contact all three at the following freeze division links or numbers:
-
- Equifax — or call 888-397-3742
- Experian — or call 866-478-0027
- TransUnion — or call 800-916-8800
You must create an account with login credentials before you can proceed to request a freeze.
- Keep your PINs in a safe place.
When you place a freeze on your credit, you’ll get PIN. You’ll need those PINs to defrost — I mean, unfreeze — your credit later. (Note: I helped a less tech-savvy client in her 80s accomplish this on Friday, and we learned that TransUnion no longer requires a PIN; your TransUnion login will suffice.)
Where you safeguard your PIN depends on the standard methods that you already use; you don’t want to be dependent upon your memory of an out-of-character decision.
- Write PINs down and put them in your fireproof safe or safety deposit box.
- Enter PINs in your digital password manager.
- Put PINs in your secure password book in code.
Do NOT put them on a sticky note affixed to the front of your computer. Do NOT write them in a little notebook that you take out of your home.
- Protect the credit files of your loved ones and those in your care
That 2018 law guarantees that you can freeze (and unfreeze) your own credit for free. (This is different from a credit lock, which requires a subscription to a credit bureaus’ services.) In addition to setting a freeze for yourself, you can obtain a credit freeze for your children under the age of 16. (Minors aged 16 or 17 may request their own freezes.)

Photo by Julia M Cameron on Pexels.com
Because minors can’t apply for loans, people rarely check children’s credit history. In theory, there shouldn’t even be a credit bureau file for a child, so when young adults start out trying to get student loans or credit cards, they may be in for a shock to learn that someone has already destroyed their credit!
For more on preventing children from being the victims of identity theft, check out:
https://consumer.ftc.gov/articles/how-protect-your-child-identity-theft
Additionally, if you serve as a conservator or guardian, or if you hold someone’s Power of Attorney, you may secure a free credit freeze for them, as well.
Why else should you get a credit freeze?
Any time you are at greater risk of identity theft, whether through a massive data breach, a run-in with a bad roommate, a breakup with a creep, or you’ve had your wallet stolen or your home burgled, a credit freeze can give you peace of mind that nobody will be able to access credit in your name.
Similarly, if elderly relatives develop dementia or anything that impairs their cognitive capacity, they can become prey to predatory lenders and charlatans selling everything from scammy auto repair warranties to non-existent services. A credit freeze prevents scams from moving past the spam stage.
Military Fraud Alerts
Members of all United States military branches have an additional resource that predates the 2018 law. They can set active duty alerts, allowing them to place a fraud alert for one year, renewable for the entirety of their deployment.
For Equifax, use the online form for an Active Duty Alert or call 800-525-6285. Meanwhile Experian has an online form but no phone number, and TransUnion has a phone number (800-680-7289) but no online form.
As a bonus, securing an active duty alert prompts the credit reporting agencies to remove a service member from the marketing lists for sneaky pre-screened credit card offers. (Service members can request to be added back, but who wants that junk mail?)
DON’T GET SCAMMED
Even partial information allows scammers to contact you, pretending they’re preventing scams. A caller might fake being from your bank or credit card, alerting you to a hacking risk. They may request you log into one of your accounts and change passwords (to something they provide) for “testing” purposes that might sound reasonable if you’ve been interrupted while chasing a toddler or running a meeting.

Photo by mohamed_hassan from PxHere
Be vigilant. If contacted by phone, text, or email, don’t respond, even (or especially) if the contact appears to already have some of your data. They’re using what they DO have to get you to reveal what they DON’T have — more of your private information. Call your financial institution directly.
The Social Security Administration won’t call you. They won’t email. They won’t text you. (Government sites may email or text two-factor authentication codes when you log into a federal site, like ssa.gov, but that’s initiated by you.)
My March post, Slam the Scam! Organize to Protect Against Scams, focused mainly on scams targeting seniors, but will help you protect yourself and loved ones from most common scams, and provides resources to help you learn more.
The Hill‘s August 15, 2024 piece, Was your data leaked in massive breach?: How to Know, and What to Do Now, has a good point about the likelihood of being at risk:
“If you’re a high-value individual that maybe has a high net worth or works at a company that they can extort you, you might actually be a real target,” Kyle Hanslovan, CEO of cybersecurity firm Huntress, previously told Nexstar. “For the masses though, the everyday common person, you’re more of a target of opportunity.”
Most people shouldn’t spend too much time worrying about what may happen if their information ends up in the wrong hands. Instead, Hanslovan recommends keeping an eye on your important accounts and making sure you’re prepared to act in case something does go wrong.
“It stinks for privacy, but it kind of normalizes just what’s happening,” Hanslovan said. “It doesn’t make it right, and it definitely doesn’t wave, you know, a company’s true fiduciary responsibilities to protect your data.”
Someone should tell NPD that.
Other Ways to Keep Bad Guys From Using Your Data to Hack You
- Make your passwords long and complex. Using at least 16 characters, with a mix of capitals, lowercase, numbers, and special symbols, will make it hard to hack you.

Image Source @2024 Hive Systems
- Use a password manager for all your longer, more complex passwords.
- Turn on two-factor or multifactor authentication for as many of your online accounts as allow it. (That’s like when you get a text or email with a code to enter before your login is authenticated.) Alternatively, you can use an authenticator app.
- Set up account alerts for your bank, investment, and credit card accounts, particularly to flag online or in-person purchases or ATM transactions outside of the US.
- Keep security software updated on your computer and phone.
- Don’t check financial accounts on insecure Wi-Fi networks; wait until you’re home, on secured WI-Fi network.
WHAT TO DO IF YOUR DATA IS USED FRAUDULENTLY
- File a police report.
- Report fraud to the Federal Trade Commission.
- If someone uses your Social Security number, report it at IdentityTheft.gov.
ONE LAST WEIRD THING
You may have noticed something odd about the class action suit. You’d expect National Public Data’s parent company to have a tech-leaning name, like InfoDynamics or Identidata.
Nope. The parent company is Jerico Pictures Inc., a Florida-based film studio owned by Salvatore (Sal) Verini, Jr., a retired deputy with the Broward County Sheriff’s office who fashions himself as an actor, producer, and writer.
Verini is also listed as the owner of companies called Trinity Entertainment Inc., National Criminal Data LLC, Shadowglade LLC (which sounds like a housing development in a horror movie produced by a company with a name like Jerico Pictures), and Twisted History LLC, which sounds like a joke.
Meanwhile, victims of data hacking won’t be doing a lot of laughing.
REFERENCES
As a Certified Professional Organizer®, I often help clients protect their identities and financial information. However, I am not a cybercrime specialist, nor do I play one on television. To research the specifics of this breach, in addition to the many government and tech-oriented links in the above post, I used a clarifying mainstream sources, including:
- 7 On Your Side steps to take to keep personal information safe amid latest data breach (WABC-TV)
- Hackers May Have Stolen Your Social Security Number in a Massive Breach. Here’s What to Know. (CBS News MoneyWatch)
- How to Check if Your Information Was Compromised in the Social Security Number Breach (Time Magazine)
- It’s Free to Freeze Your Credit: Here’s What You’ll Need to Do (HerMoney.com)
- The Weirdest ‘3 Billion People’ Data Breach Ever (The Verge)
- What to Know about Credit Card Freezes and Fraud Alerts (FTC.gov)
Keep your eyes open and your personal information close to the vest.




Such great advice, Julie! I have had a credit freeze on my credit for years now. I even have an alert at my bank instructing the teller to check the ID of anyone asking to deposit or whithdraw from my account because several of my accounts were breached in 2014. It took some time to change all of my account numbers and get everything returned to me.
That’s fabulous that you’ve had your freezes in place for so long. It’s a wonderful way to have peace of mind; I understand why some people at certain stages of their lives (young parents, buying cars and homes, for example) who need to keep their files unfrozen may opt for the fraud alerts, but I’m recommending this as a standard action going forward.
I’m glad everything finally worked out for you.
Great stuff! Thank you for all the work you did to put this together in one post. I especially liked the pentester.com website. I’m going to be sharing this with my decluttering group today. =)
Thanks for reading, and I love knowing that you’ll be sharing this. Thank you!
There was a lot of background to suss out, but understanding what’s going on outside of our view has been really instrumental for accenting the vital importance of protecting credit files.
What a sobering post! There is so much excellent research, actionable items, and great information here. Thank you for this comprehensive deep dive into the breach.
I did a quick search on pentester.com and was relieved to find no breaches. I’ll review the following steps to see what needs to be done. Oy.
Sobering content, yes, which is why I tried to add as much humor as possible. Hopefully David Hasselhoff and Pauley Shore will forgive me. 😉
I must have read fifty articles from across four months to finally get an accurate picture of what happened, but it was worth it to get a sense of the real risk. And wow, you are the first person I’ve found (out of about 30) whose name did not appear in the breach. That’s lucky!
Thank you for reading!
Reading this just makes me nauseous. Thanks for the detailed information and links. I’ll be following up to make sure I’m securely frozen up.
By the way, letting you know that I passed on your passport renewal post to 2 people, one of whom has already received her renewal… so thanks so much for all your current, important, relevant information!
Hey, I acknowledge the queasy sensation right in the post. The more we know about how the sausage is made (that is, the way our data gets handled, even by the — well, I won’t call them good guys, maybe neutral guys?) the ickier we feel, and perhaps the more likely we are to take actions to protect ourselves. At least that’s why I wrote this.
And Seana, thank you SO MUCH for your feedback. I have no desire to monetize my blog (though it is intriguing), but I get so much joy from knowing people are using my advice. I really appreciate you telling me this.
Thanks for reading, and I’ll pass the Dramamine!
Wow Julie. Great information. I feel like it’s impossible for you digital identity to always be safe these days.
I think you’re right, Janet. The best we can do is to protect ourselves from the greatest harm, because our information just can’t be protected. The bad guys are always one step ahead, technologically-speaking.
Thank you for reading!
Just wanted you to know that I was in the middle of re-freezing my credit (one company was still frozen and I can’t remember why I unfroze the other two) when I was notified of this “new” breach by IDNotify (related to my TurboTax account). My point is that you beat them to the punch! I was also already working my way through some old password manager accounts (some to change the PW, others to delete). Now I need to figure out who all I need to help with this issue. Thanks for the shareable blog post!
Whee, I’m glad to be on the forefront, though this is one area where I’d have been happy if there were no news to share. I was considering writing this for August 19th, but I’m glad I waited, as more details kept coming out through last week. And I know I could have just written the How-To part of the post, but I find the context scarily fascinating.
I know you’ll help lots of people. And thank you for reading. I’m glad you’re re-freezing.
Wow. What an amazing post. The only thing missing is the button that says hire me to help walk you through all of this. The world needs that button.
LOL, thank you for the praise, Melissa. While there’s no Staples’ Easy Button for this, I’ve been gratified helping clients work through the process.
It’s not difficult or (too) time-consuming, but there’s a lot of create login/get 2-factor authentication code/reply with code/log in/set up account folderol before requesting the freezes. What we really need are harsher penalties for people who scam and steal, and a way to lock the bad guys out of systems. Sigh.
Julie, thank you for doing all this research. It’s certainly not in the local newspaper! Since I experienced identity theft, I’ve frozen and locked my Experian Account and the other two. Yes, it’s a pain when I want to add a credit card, but given that I spent over a year deleting the misinformation in my records and got back every last dollar used to buy items or withdrawn from my bank account, it is worth the small inconvenience. Thanks for warning everyone!
It sounds like you’ve done all the right things, no matter how frustrating, in the aftermath of your identity theft experience. I’m sorry you went through that.
Thank you for your kind words; this was a meaningful post to research because it has such dire consequences. We can only hope the security community will come up with less easily breakable ways to contain our information safely.
Thank you so much, Julie!! This is the most thorough article I’ve seen about the NPD breach since I’ve been reading about it. I changed my Social Security password and a few others but need to do more. I’ve also started using the long convoluted passwords created by 1Password. I’ve had a freeze on my credit accounts for over 10 years.
Thanks for reading Susan, and for the kind words. I think we all need to improve our password hygiene process, at least until the security community comes up with solutions that are satisfying for everyone. I prefer using thumbprint or facial ID recognition, but those are still (for now) based in having a password supplied on our behalf, and authentication apps are merely one step above two-factor authentication. We’ll have to keep striving until the security guys get it together!
Wow. Julie. You are a rock star and our hero. Amazing that you were able to explain this in an a-z way, in language that we can actually understand!!! I am your fan forever. And no, an aspirin will not be enough.
Thanks so much, Judy. My posts are usually research heavy, but this one took a lot of reading over ten days just to get the chronology straight. I’m sure we’ll learn more in future days, but at least the how-to aspect is fairly straightforward.
I suspect we’ll need a lot of aspirins until the security community comes up with something better.